
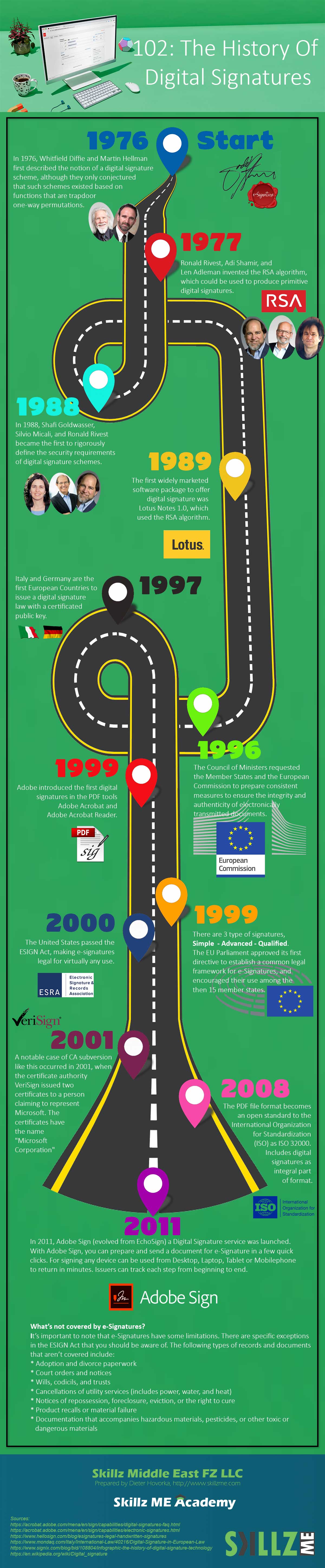
Good things in life take a while and the same applies to the long way from an e-Signature to Digital Signature. In the journey of the history of digital signatures we highlight key events, the key people and companies adopting technology in usable applications. Let the journey begin.
Digital Signature has the agenda to allow signing electronic data and documents with a unique e-Signatures which uses encryption and a public key managed by a certification authority (CA). In most cases, digital signatures are following a national law in a country where the document shall be legally accepted. We want to look behind the scenes and see, where does the idea come from and what was the journey of developing a digital signature and it’s law across the globe.
It all started back in 1976 when Whitfield Diffie and Martin Hellman first described the notion of a digital signature scheme, although they only conjectured that such schemes existed based on functions that are trapdoor one-way permutations.
In 1977, Ronald Rivest, Adi Shamir, and Len Adleman invented the RSA algorithm which is until today the most common digital signatures algorithm. In the early stage It was used to produce primitive digital signatures (although only as a proof-of-concept – “plain” RSA signatures are not secure). Their privately held company RSA Security was founded later in 1982. Later in 1995 RSA Security was involved in the launch of Digital Certificates International, better known as VeriSign.
In 1988, Shafi Goldwasser, Silvio Micali, and Ronald Rivest defined the security requirements of digital signature schemes. They described a hierarchy of attack models for signature schemes. This was the beginning of making e-signatures more secure.
In their original released document, Goldwasser, Micali, and Rivest lay out a hierarchy of attack models against digital signatures:
- In a key-only attack, the attacker is only given the public verification key.
- In a known message attack, the attacker is given valid signatures for a variety of messages known by the attacker but not chosen by the attacker.
- In an adaptive chosen message attack, the attacker first learns signatures on arbitrary messages of the attacker’s choice.
A certificate authority (CA) issues digital certificates that contain a public key and the identity of the owner. Today a variety of over 200 non-profit and commercial CAs exist.
In 1989, Lotus Notes 1.0 was born and raised on the market. Lotus Notes was the first software that was using digital signatures with RSA algorithm.
Finally, in 1996 the European Commission laid the foundation for its 15 member states to prepare consistent measures to ensure the integrity and authenticity of electronically transmitted documents. The legal framework for an e-signature and document signature.
Only one year later 1997, Italy and Germany have been the first countries issuing a digital signature law based on a registered public key.
Adobe introduced the first digital signatures in the PDF tools Adobe Acrobat and Adobe Acrobat Reader in the year 1999. The digital signature came with encryption and got registered with ESTI. The international standard known as PAdES (PDF Advanced Electronic Signatures) is now the basis for billions of signature transactions every year.
In 2000, the United States passed the ESIGN Act, making e-signatures legal for virtually any use. It was the foundation for many countries to follow with their national standards to be issued.
Digital Signatures are relying on CAs which can be in the middle of a planned fraud. In the history of digital signatures, a notable case of CA subversion like this occurred in 2001. The certificate authority (CA) VeriSign issued two certificates to a person claiming to represent Microsoft. The certificates have the name “Microsoft Corporation”, so they could be used to spoof someone into believing that updates to Microsoft software came from Microsoft when they actually did not. Microsoft and VeriSign took steps to limit the impact of the problem.
In 2008, the PDF document format invented by Adobe becomes an open standard to the International Organization for Standardization (ISO) as ISO 32000. This standard includes digital signatures as an integral part of the format. This allows many implementations and new software solutions to utilize the document standard PDF.
In 2011, Adobe Sign (evolved from EchoSign) a cloud-based digital signature service was launched. With Adobe Sign, you can prepare and send a document for e-Signature in a few quick clicks. For signing any device can be used from Desktop, Laptop, Tablet or Mobilephone to return in minutes. Issuers can track each step from beginning to end.
It’s important to note that e-Signatures have some limitations. There are specific exceptions in the ESIGN Act that you should be aware of. The following types of records and documents that aren’t covered include:
- Adoption and divorce paperwork
- Court orders and notices
- Wills, codicils, and trusts
- Cancellations of utility services (includes power, water, and heat)
- Notices of repossession, foreclosure, eviction, or the right to cure
- Product recalls or material failure
- Documentation that accompanies hazardous materials, pesticides, or other toxic or dangerous materials
However, every country has it’s own digital signature law and the list of accepted documents to be electronically signed might be different from the list above.
Digital Signature is not limited to documents and files. You can use them to sign in the simplest way a data stream or data package. Digital signatures solutions get more practical if they can be visualized and validated in a simple way. Also, there are a lot of solutions that isolate the signature vs embedding the digital signature into the original data package.
Our 102: The History of Digital Signatures shows that good things get developed over time to reach a certain functional and practical level. We have learned about names we did not hear before and players on the market which we did not calculate into the equation.

![Formula 1’s Highest-Paid Drivers 2024 [Infographic] hero-image-Formula1-Highest-Paid-Drivers-2024](https://www.skillzme.com/wp-content/uploads/2024/12/hero-image-Formula1-Highest-Paid-Drivers-2024-200x200.jpg)

![Human Wonders Apollo 13 - Houston we have a Problem [Infographic] hero-image-Apollo-13-mission](https://www.skillzme.com/wp-content/uploads/2025/01/hero-image-Apollo-13-mission-200x200.jpg)


Recent Comments