

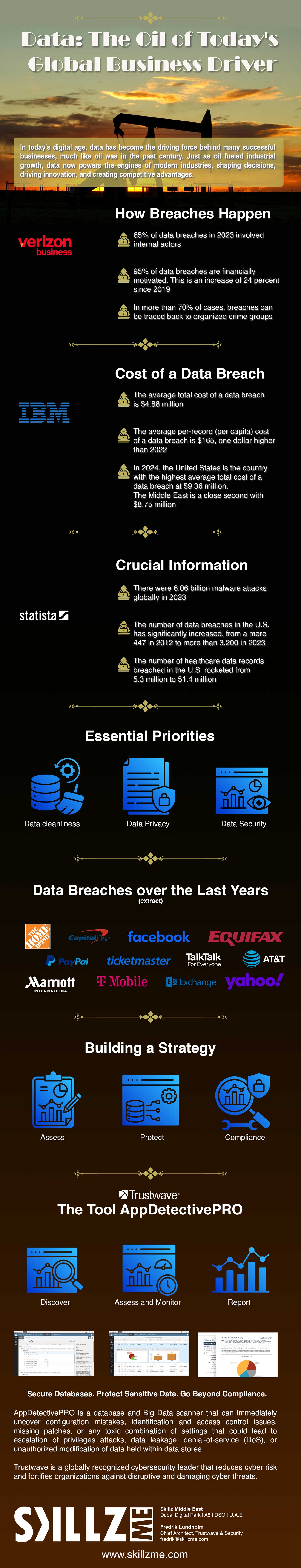
Big Data is the Oil of Today and the Biggest Global Business Driver. A barrel of oil today is a measurement for many people where the world economy stands. For me, data is still the number 1 success factor for any size of organization. It starts with data cleanliness, the security of data, and not forgetting the privacy. I want to look into the aspect of what drives us today to protect the oil of today in our organization.
Big Data is the oil of today. Many companies have realized that having the right data and using it effectively can enhance their value proposition, boost income, improve reputation, strengthen customer relationships, and more, all of which are crucial in today’s competitive global market. Therefore, it’s essential to ensure that your data is well-protected against malware, theft, and even internal attacks.
When it comes to Data, I see 3 Essential priorities:
 Data cleanliness
Data cleanliness
When it comes to data cleanliness, there are several key aspects that I focus on to ensure the quality and reliability of the data I work with.
First, accuracy is crucial for me. I ensure that the data I use accurately reflects the real-world values it represents. If the data is incorrect, it can lead to misleading conclusions and poor decision-making.
Next, I pay attention to consistency. I make sure that the data is uniform across different datasets and formats. Inconsistent data, such as conflicting information or varied formats, can create confusion and affect the effectiveness of the data analysis.
Completeness is another key aspect I focus on. I ensure that no critical information is missing, as incomplete data can lead to gaps that impact analysis or operations. I always check that all the necessary fields are filled and that the dataset is whole.
Additionally, I monitor uniqueness. I ensure that there are no duplicate entries, as duplicates can distort analysis and reports.
Lastly, I make sure the data is valid. This means it adheres to the correct formats, ranges, or predefined standards. I regularly check that values fall within expected parameters and avoid any invalid entries.
 Aspects of Data Privacy (In My View)
Aspects of Data Privacy (In My View)
When I think about data privacy, there are several critical aspects that I focus on to ensure personal and sensitive information is protected and managed responsibly.
First, confidentiality is vital to me. I make sure that sensitive data is only accessed by authorized individuals. I take extra care to prevent unauthorized access, sharing, or misuse of data. This ensures that the information I handle remains private and secure.
Data minimization is another key aspect I prioritize. I only collect the necessary data needed for a specific purpose, avoiding the collection of excessive or unnecessary information. By minimizing the data I gather, I reduce the risks of misuse or breaches and ensure that the data stored serves its intended function without putting privacy at risk.
Integrity is something I take seriously. I ensure the data I handle remains accurate, unaltered, and consistent unless changes are authorized. This helps maintain data reliability and prevents manipulation or corruption of information.
Accountability is also a core principle for me. I take responsibility for making sure the right measures are in place to protect data. Regular audits and compliance checks are essential to ensure that privacy protocols are followed and that data is handled in line with the necessary regulations.
Lastly, transparency is essential. I make sure individuals whose data I manage are well-informed about how their data is being used, stored, and protected. By being transparent, I help build trust and ensure individuals are aware of their rights regarding their personal data.
Regulations on Data Privacy
In terms of regulations, the European Union (EU) has established some of the strictest data privacy rules through the General Data Protection Regulation (GDPR). The GDPR is designed to protect personal data and privacy for individuals within the EU and applies to any organization handling the data of EU citizens, regardless of where the organization is located.
In the United States, however, there is no comprehensive federal law like the GDPR. Instead, there are sector-specific laws, such as the California Consumer Privacy Act (CCPA), which applies to businesses operating in California and protects the privacy rights of California residents. Other regulations, like the Health Insurance Portability and Accountability Act (HIPAA) focus on the protection of health data, while the Children’s Online Privacy Protection Act (COPPA) protects children’s privacy online.
One of the challenges in the U.S. is the lack of a single federal data privacy law. Instead, states like California have developed their own laws, creating a fragmented regulatory landscape where different rules apply depending on the state. This inconsistency makes it difficult for businesses to ensure compliance across the country.
Why Is Data Privacy Not a Major Topic in China and Asia?
Data privacy has not traditionally been a significant topic in China, primarily because the government has historically emphasized control over individual privacy. The Asian governments prioritize national security and economic control over individual privacy rights. In China, data is often collected and used for purposes of surveillance and governance rather than for protecting individual privacy.
With the increasing reliance on data in Asia’s rapidly developing economies, the conversation about data privacy and breaches is starting to gain momentum, especially with new regulations like China’s Personal Information Protection Law (PIPL).
 Data Security
Data Security
The security of our oil of today should be a number 1 concern. This makes it a major topic, violation can harm financially, reputation and ofcourse could bring us out of business. Here are a few well-known examples of companies that experienced significant data breaches or cyberattacks in the last ten years:
- Home Depot (2014)
In 2014, The Home Depot experienced a significant data breach that compromised 56 million payment card records. The breach was carried out using a “unique, custom-built malware,” which infiltrated the retailer’s systems, allowing hackers to steal customers’ payment card information. - Capital One (2019)
In 2019, Capital One suffered a massive data breach affecting over 100 million customers. The hacker exploited a vulnerability in the company’s cloud infrastructure, stealing personal data, including names, addresses, credit scores, and bank account numbers. This breach is one of the largest in history. - Marriott International (2018)
In 2018, Marriott International reported a breach of its Starwood guest reservation database, which had been ongoing since 2014. The breach exposed the personal information of around 500 million customers, including passport numbers, credit card information, and more. - T-Mobile (2021)
In 2021, T-Mobile experienced a breach that compromised the personal data of over 40 million current customers. The hacker gained access to sensitive data, including names, dates of birth, social security numbers, and driver’s license information. The breach also affected 7.8 million customer accounts. - AT&T (2024)
AT&T has officially acknowledged that it was affected by a data breach involving 73 million current and former customers, after previously denying that the leaked data came from their systems. In a statement, the company said, “According to our preliminary analysis, the data appears to date back to 2019 or earlier, affecting around 7.6 million current AT&T account holders and about 65.4 million former account holders.” - PayPal (2025)
The New York State Department of Financial Services has announced that PayPal will pay $2 million in a settlement for failing to adhere to security rules and regulations. The security breach occurred three years ago, but it took the company that long to acknowledge any fault, settling the case for a fraction of their profits. The breach exposed personally identifiable information (PII) while PayPal attempted to keep the attack hidden from the public. As part of the settlement, PayPal has agreed to improve its cybersecurity practices and comply with state regulations.
These breaches highlight the critical importance of securing data against both external and internal threats. The impact of these incidents often extends beyond just the immediate loss of data, affecting brand reputation, customer trust, and financial stability.
As I can see, data breaches occur across all regions, from the US to the EU. However, I might not have full transparency or insight into what happens in Asia, or at least, I haven’t come across any examples yet.
The Year 2024?
Almost every month in 2024 brought a new, shattering cybersecurity headline. 2024 was one of the most significant years in the global IT and security landscape for me. The attacks that disrupted critical services and impacted daily life, and whose consequences are still unfolding into 2025, grabbed attention everywhere.
If I look back at our monthly compilations of the biggest cyber attacks 2024, data breaches, and ransomware incidents, it’s clear what I’m referring to.
So you ask yourself,
How to protect your Oil of Today?
Make it Number 1: Take it seriously and make it a CxO topic!
Focus on a Solid Strategy; I can help mitigate the risks associated with data privacy and data security challenges, ensuring that sensitive information is well-protected while maintaining compliance with regulations.
Building a Strategy with the Right Tool
Looking at the market and executing a proper strategy brought my attention to Trustwave AppDetective. Trustwave AppDetective is a database security tool designed to help organizations assess, protect, and maintain compliance for their databases.

Here are the top 10 Features of Trustwave AppDetective:
- Comprehensive Database Security Assessment
I can scan databases to identify vulnerabilities, misconfigurations, and insecure practices. It provides detailed insights into security gaps, such as weak passwords, default accounts, and unpatched systems. - Regulatory Compliance Support
Trustwave AppDetective helps me meet compliance requirements for regulations like PCI DSS, HIPAA, GDPR, and SOX. It generates reports that demonstrate compliance with key security standards. - Discovery and Inventory of Databases
The tool automatically discovers databases across my environment, including unauthorized or untracked (“rogue”) databases. It helps me maintain an up-to-date inventory of all database systems in my network. - Risk Scoring and Prioritization
AppDetective assigns risk scores to vulnerabilities and configurations, allowing me to prioritize remediation efforts based on the criticality of each issue. - User Rights and Permissions Analysis
It helps me identify excessive user permissions and privileges that could lead to security breaches. It ensures that access is granted strictly on a “need-to-know” basis. - Continuous Monitoring
I can regularly scan databases to detect new vulnerabilities or changes in configurations, ensuring ongoing security and compliance. - Ease of Use
With intuitive dashboards and detailed reports, I can easily analyze findings and take necessary actions. The non-intrusive scans ensure minimal disruption to database operations. - Supports Multiple Database Platforms
Trustwave AppDetective works with a wide variety of database management systems (e.g., Oracle, SQL Server, MySQL, DB2), making it versatile for diverse IT environments. - Integration with Security Ecosystems
The tool integrates seamlessly with other Trustwave products and third-party security solutions to enhance the overall organizational security posture. - Cost Savings
By reducing the likelihood of costly data breaches and non-compliance penalties, Trustwave AppDetective streamlines security operations, reducing manual effort and saving both time and resources.
By leveraging Trustwave AppDetective, I can proactively secure databases, reduce risks, and ensure regulatory compliance in a streamlined manner. Do you also feel that data is our oil of today, and we should take care of it and keep it safe? Share your thoughts in our commenting section below. Unsure is your data is safe, you need transparency; contact me/us for an assessment.
I am a Chief IT Architect focused on new solution offerings in the Gulf, Levant, Saudi Arabia and Pakistan. I deliver successful business outcomes working closely work with my Vendors and Partners in the local countries and colleagues to translate business requirements to commercially viable architecture.

![How EDI has Impacted Different Industries [Infographic] How EDI has Impacted Different Industries](https://www.skillzme.com/wp-content/uploads/2025/02/banner-EDI-Impacted-Different-Industries-200x200.jpg)
![Formula 1’s Highest-Paid Drivers 2024 [Infographic] hero-image-Formula1-Highest-Paid-Drivers-2024](https://www.skillzme.com/wp-content/uploads/2024/12/hero-image-Formula1-Highest-Paid-Drivers-2024-200x200.jpg)
![United Arab Emitaes (UAE) Population Statistics 2024 [Infographic] hero-image-UAE-Population-Statistics-2024](https://www.skillzme.com/wp-content/uploads/2024/11/hero-image-UAE-Population-Statistics-2024-200x200.jpg)


Recent Comments