Data Security
with AppDetectivePRO
2024
Was the year of the most data Breaches
-
The average cost of a data breach reached in 2024 of $4.88 million
-
Nearly half (46%) of all breaches involve customer personal identifiable information
-
It takes organizations an average of 204 days to identify a data breach
Database Security Audit and Risk Assessment Service

Databases hold an organization’s most important information assets, often referred to as the “crown jewels”. Databases are critical repositories of customer information and intellectual property and are sought-after targets for cybercriminals. We in Skillz Middle East understand the importance of always having data secure with the continuously evolving cybersecurity threats. Our Database Security Audit and Risk Assessment helps you to stay on top of global market threats.
Protect Data on Premises and in the Cloud
With Trustwave we can assess and monitor databases on promises or in your cloud migration path, whether hybrid or in the public cloud.
Comply with Regulations in Over 80 Countries
Ensure regulatory compliance across the globe for GDPR, PCI NIS 2, HIPPA, CCPA, with over 1,700 pre-built data classifiers and policy templates.
Identify Data in Motion, at Rest, in Use and in the Cloud
Discovery, classify, prioritize, protect and monitor data without impacting the user experience. Get visibility into your data and its movement across your organization.
Prevent Data Breaches Before They Occur
Go beyond compliance and implement security best practices backed by monthly knowledge base updates powered by Trrustwave SpiderLabs.
Streamline Policy Management
Sophisticated user and application rights management engineer to untangle complex access rights enable the least privilege principle and support zero trust policy.
Remediation Guidance
Provide remidation guidance, so security personnel do not need to be experts on all databases. Identify wrong-configured security groups and accounts.
Eliminate threats quickly and precisely
Trustwave optimizes your current security infrastructure to help you get the most value from your existing tools.
-
- Combat active threats with regular security bulletins from SpiderLab
- Strengthen your team with experienced cybersecurity professionals
- Minimize risk by fortifying your defensive posture
Robust Protection
Provide robust protection with minimal impact of databases performance
Elite SpiderLabs Threat Intelligence
Benefit from a unique understanding of the threat landscape
Known & Unknown Threat Detection
See beyond IoCs to identify behavioral threats undetected by cyber technologies
Thorough Incident Investigation
Eradicate threats through comprehensive context-based investigation enabled by AI
Rapid & Effective Responses
Contain & mitigate threats quickly before damage is done
Client-Informed Decisions
Take response actions as an extension of your team through client-driven protocols
Globally recognized by industry analysts as a leading MDR (Managed Detection and Response) provider.
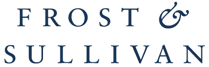 |
Trustwave named in 2024 Gartner
Market Guide for Managed Detection & Response
Proactive Database Security for a Data-Driven World
Secure Databases. Protect Sensitive Data. Go Beyond Compliance.
Proactively prevent database breaches and go beyond just meeting your database compliance requirements with database assessment, risk visibility, continuous data protection, remediation guidance and active response capabilities for your on-premises and cloud databases.
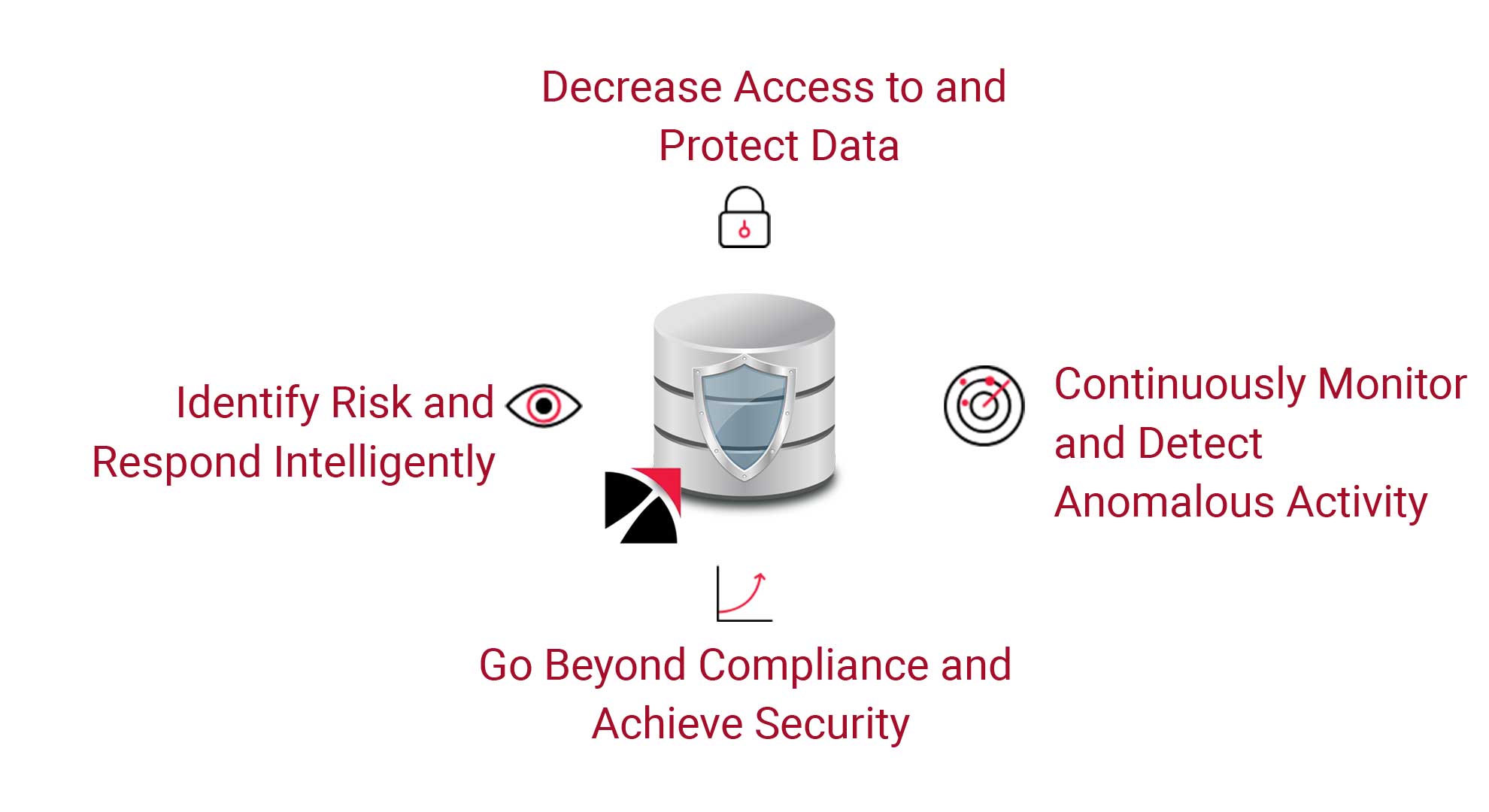
AppDetectivePRO Database Security Benefits
Many Security and IT departments are overwhelmed with the growing list of cyber security demands. With limited staff and expertise in database security, organizations are often only able to focus on maintaining compliance.
Data The Oil of Today and Global Business Driver
Fredrik Lundholm, Chief Architect, Trustwave & Security is highlighting in the Skillz Blog the security concerns when it comes to data security and where the global measures are important. Furthermore, he highlights aspects like data privacy, regulations and, data cleanliness.


Raising the Bar for Comprehensive Security Assessments
For more than a decade, Securance Consulting has leveraged Trustwave AppDetectivePRO to help clients assess risk and compliance. During this time, cybersecurity has evolved from a nascent topic to one at the forefront of business risk prevention. Learn how Trustwave equips Securance Consulting with a powerful tool that is a foundational component of their enterprise-wide IT assessments.
Database Security Solutions to Meet Your Needs
Trustwave delivers the flexibility needed to protect your databases or the option to have it managed by the only company recognized by Gartner, IDC and Forrester as a leading global Managed Security Service provider.
AppDetectivePRO
The preferred tool for security practitioners, is a database security audit and assessment scanner that can be downloaded and installed on a workstation in minutes. Scan your database and understand your risk by uncovering configuration issues, vulnerabilities, elevated data access or any combination of settings that could potentially compromise the integrity of the database.
DbProtect
DbProtect is a visual database security and risk management platform that helps organizations secure their enterprise databases – on-premises or in public, private or hybrid clouds. DbProtect is used by enterprises, government organizations and small and medium-sized businesses, to automate two labor-intensive, best practices: continuously assessing for database risk and continuously monitoring database activity.
Database Security Risk Assessment
Extend your team’s ability to eradicate database threats by leveraging Skillz Middle East’s renowned security experts to manage Trustwave DbProtect for you. Increase productivity in managing database threats and gain greater visibility into the full spectrum of the attack chain.
Get Started
Learn more about how our specialists can tailor a security program to fit the needs of your organization.
FAQs
What is a Managed Detection and Response service?
Managed detection and response (MDR) is a cyber security service that helps companies process and respond to alert data coming from various security tools in their environment. MDR helps companies identify benign alerts, or “false positives” and quickly home in on those that represent credible threats. Most MDR providers will then alert the client’s security team to the threat, leaving it to them to respond. Others will aid clients in responding to the incident.
What are the benefits of an MDR service?
An MDR provider can deliver numerous benefits, including:
- Improve your threat visibility across your environment, including hybrid cloud infrastructure
- Eliminate active threats on a 24×7 basis
- Extract more value from your existing security solutions by making them more effective
- Detect and respond to threats more quickly, and with more precision
- Improve your security posture by finding sophisticated threats, including persistent threats and intruders who are embedded in your environment
- Augment your internal security team with additional security professionals
The benefits obtained from using MDR providers are so significant that Gartner estimates 50 percent of organizations will be using MDR services by 2025 and that the market is growing at a rate nearly five times that of other managed security service (MSS) offerings.
I’ve got lots of security tools. Why do I need an MDR service?
Investing in security solutions such as endpoint detection and response (EDR), security information and event management (SIEM), and security orchestration automation and response (SOAR) platforms is a wise choice. Each of them plays a crucial role in an overall cyber security strategy by generating alerts when they detect suspicious activity in your environment and helping you with threat management.
Often, however, the number of alerts they generate is too large for companies to effectively deal with, especially since most of them are false positives. That makes it difficult for organizations to filter through the alerts and find those that represent credible threats.
A good MDR provider will ingest high value telemetry from your existing security tools, correlate alerts coming from across the environment, eliminate false positives, and zero in on alerts that are indicative of an actual threat. So, an MDR service complements the security tools you already have, helping you parse the alerts they generate so you get more value from them.
I’m using multiple cloud-based services and still have significant on-premises infrastructure. Can a single Managed Detection and Response service cover all of that?
Yes. Trustwave MDR can span hybrid cloud environments that include multiple cloud providers as well as on-premises infrastructure. It’s all configured to appear as a single logical environment to Trustwave, so alerts are correlated for investigation context across all of the infrastructure.
I’m already spending a lot of money on cyber security. How can I cost-justify a Managed Detection and Response service on top of everything else?
MDR (Managed Detection and Response) ensures you get the maximum value from your security tools and platforms by making sure they deliver on their intended purpose. While having EDR, SIEM, SOAR, and other tools is beneficial, they only provide value if you can actively respond to the alerts and insights they generate. Many organizations struggle here due to a lack of in-house security expertise to monitor alerts 24/7. A reliable MDR provider steps in as an extension of your security team, providing continuous monitoring of your security tools. Top MDR providers also incorporate proprietary threat intelligence and assist with remediating the threats identified by your security tools. Ultimately, the true value of any security tool comes from effectively addressing and mitigating threats, and MDR ensures you fully capitalize on the tools you’ve already invested in.
What are the key attributes to look for in a Managed Detection and Response provider? What questions should I ask prospective providers?
When evaluating an MDR provider, there are several key attributes to consider as essential benchmarks. These include a solid track record of experience, which is reflected in the number of years in business and the retention rates of security staff. The provider must also have the necessary resources, such as a well-staffed team and multiple security operations centers (SOCs), to ensure 24/7/365 coverage. A global presence is crucial—even if you’re not a global company—because it provides visibility into emerging threats from anywhere in the world. Additionally, an MDR provider with an active threat hunting team is highly valuable, as it proactively searches for threats that might evade detection by traditional security tools. Ideally, these hunters should be capable of identifying both indicators of compromise (IOCs) and indicators of behavior (IOBs).
To assess whether a provider meets these standards, consider asking the following questions:
- How long has the vendor been offering MDR security services?
- How does the vendor attract, retain, and train its staff? What certifications do its security professionals hold?
- Can the provider consistently respond to threats quickly, or are there differences in expertise across SOCs or analysts?
- Does the provider have processes that enhance its expertise beyond individual talent?
- What is the provider’s geographic and industry reach? Does it have global threat intelligence or focus primarily on specific regions or sectors?
- What threat intelligence sources are incorporated into its MDR services? Does it operate its own security research lab?
- Does the vendor handle response actions, and is that included in the service package or offered as an additional cost? How does the vendor ensure compliance with your security policies?
- How well is the provider recognized within the cybersecurity industry?
- Do its supported technologies and platforms align with your existing environment?
- What communication channels are available to interact with the service (email, ticketing, phone, mobile app)?
- What industry certifications and standards does the vendor adhere to for supporting your compliance and maturity objectives?
- Does the vendor offer additional managed services like threat hunting, digital forensics and incident response (DFIR), or consulting?
These questions will help you evaluate the experience, capabilities, and value a potential MDR provider can bring to your security strategy.
How long will it take me to get started with a Managed Detection and Response provider?
The onboarding process can vary significantly between providers, with the best ones offering clear, structured procedures that help clients quickly start seeing value from the service. For example, Trustwave ensures that each client has a dedicated Cyber Success Team to onboard them in 10 days or less, continually optimizing the environment for peak performance and results. We believe our onboarding process is such a key differentiator that we created an e-book to provide a detailed explanation of it.
