IRM
Information Rights Mangement
Protect the integrity and privacy of sensitive information no matter where it travels with Information Rights Management (DRM/IRM). Improve your regulatory compliance posture and client satisfaction in a single step.
Digital Rights Management (DRM) is a class of technologies that are used by hardware manufacturers, publishers, copyrights holders, and individuals with the intent to restrict the use of digital content. Nevertheless, there are many competing definitions. With first-generation DRM software had the intent is to control copying. With second-generation DRM, the intent is to control executing – viewing — cut and paste — printing and altering of content or documents. The term is also sometimes referred to as copy protection, copy prevention, and copy control, although the correctness of doing so is disputed. Companies such as Amazon, AT&T, AOL, Apple Inc., Google, BBC, Microsoft, Electronic Arts, Sony, and Valve Corporation use digital rights management.
DRM and documents
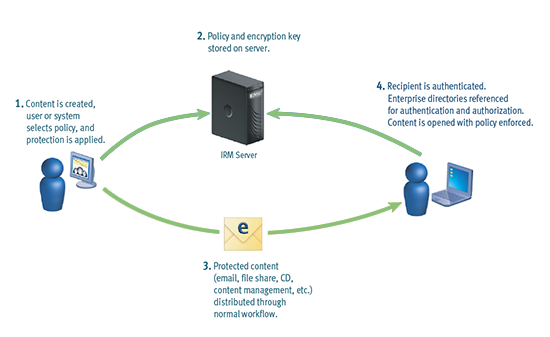
Enterprise digital rights management (E-DRM or ERM) is the application of DRM technology to the control of access to corporate documents such as Microsoft Word, PDF, and AutoCAD files, emails and digital media rather than to the control of consumer media. E-DRM, now more commonly referenced as IRM (Information Rights Management), is generally intended to avoid the unauthorized use (like industrial or corporate espionage or inadvertent release) of proprietary documents.
IRM typically integrates with Content Management System or Digital Asset Management software.

Mobility and secure access
IRM secure access to sensitive documents via iPad and iPhone anytime, from anywhere.

Dynamic Policy Control
IRM allow content owners to define or change information rights and recall or expire content after distribution

Persistent Protection
Information Rights Management (IRM) provides security for documents, messages, and attachments while in transit, at rest, and after delivery.

Continuous Audit Trail
IRM track all activity associated with secured content to demonstrate proof of compliance with security policies.
Skillz Middle East helps lower the risk of sensitive information falling into the wrong hands. Dynamic policies let you secure critical information, improve your regulatory compliance posture, and extend the collaboration sphere for communications inside and outside the firewall. Additionally, IRM solutions have arrived into the mobile realm. Persistent security ensures documents stay protected, whether users are online or offline.
We analyze your needs, infrastructure and information type to select the particular technology for your organization never losing the mission out of our eyes.
Skillz Middle East helps lower the risk of sensitive information falling into the wrong. Dynamic policies let you secure business critical information, improve your regulatory compliance posture, and extend the collaboration sphere for communications inside and outside the firewall. Additionally, IRM solutions have arrived into the mobile realm.
We analyze your needs, infrastructure and information type to select the particular technology for your organization never losing the mission out of our eyes.
Useful Links
![]() Adobe LiveCycle Rights Managment click here
Adobe LiveCycle Rights Managment click here
![]() EMC Information Rights Management Data Sheet click here
EMC Information Rights Management Data Sheet click here
![]() Microsoft Rights Management services click here
Microsoft Rights Management services click here